The GCP cloud config source takes configuration properties from GCP Secret Manager.
GCP Service Account
In order to connect to GCP Secret Manager you need to know your project name as well as have a service account access token. Assuming you already have a GCP project and a secret created in GCP Secrets Manager, you need to create a service account which Payara Server will use to access your GCP Secrets.
Visit the GCP cloud console: https://console.cloud.google.com/
Firstly, make sure you’re on the right project. You can find your project name at the top of the GCP console.

Next, visit the service account section of the project. You can find this from the top left menu → IAM & Admin → Service Accounts.
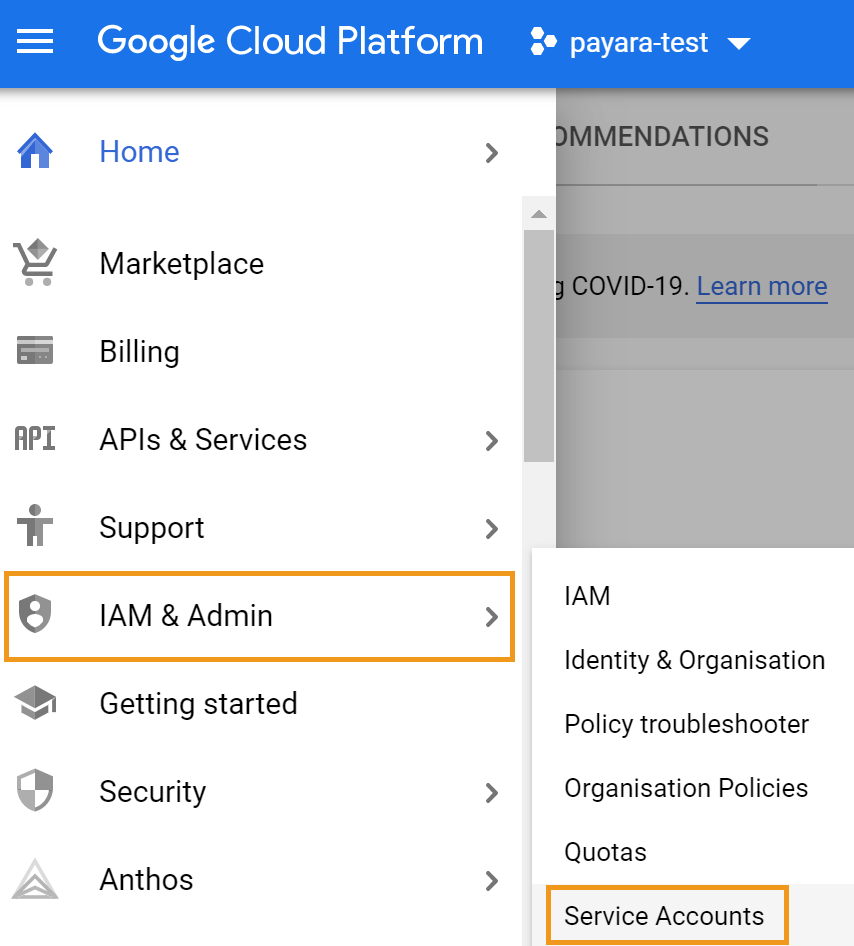
From here you can create a new service account. Skip this step if you already have a service account you want to use.
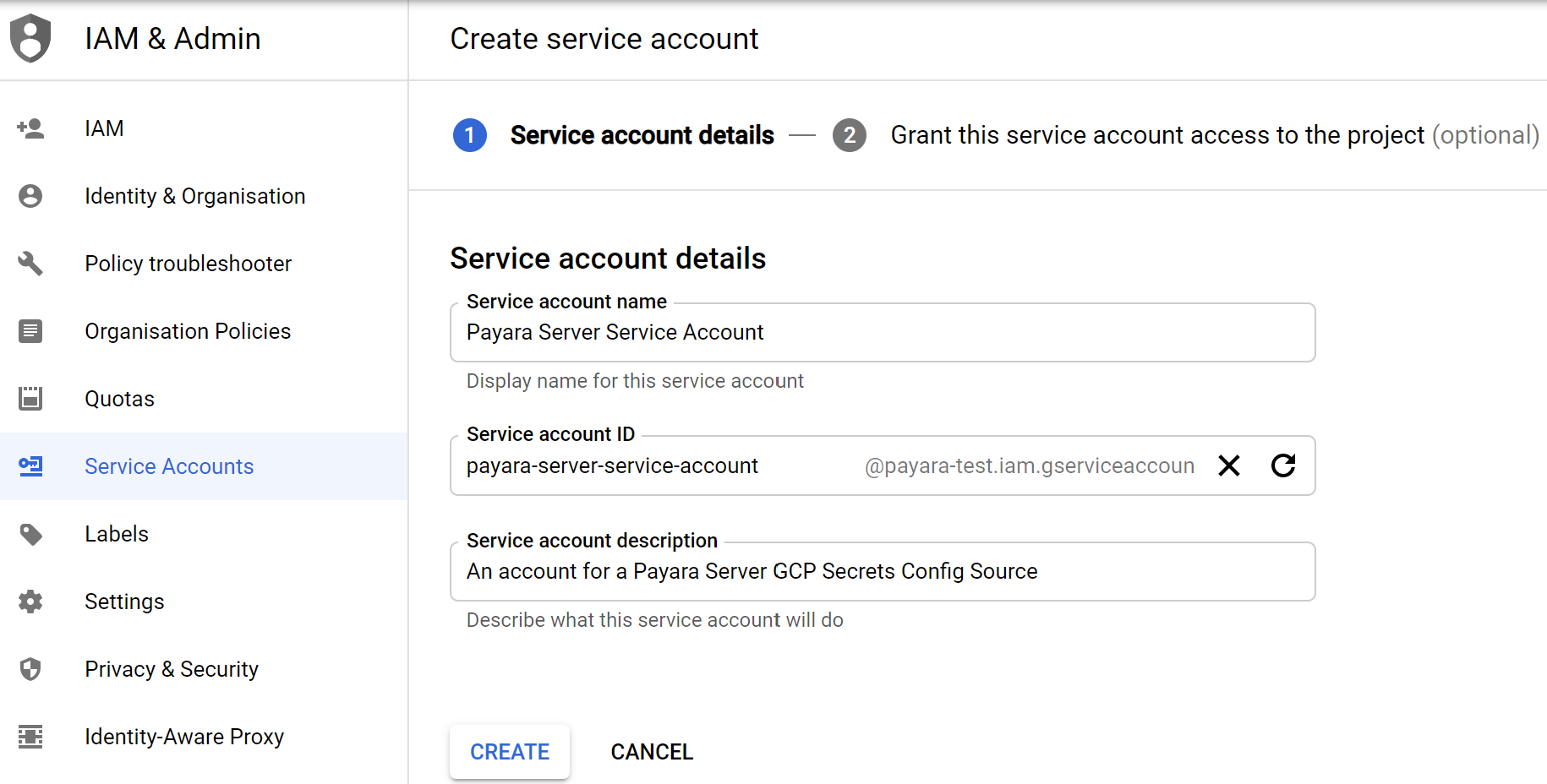
After this you’ll need to add roles to your service account
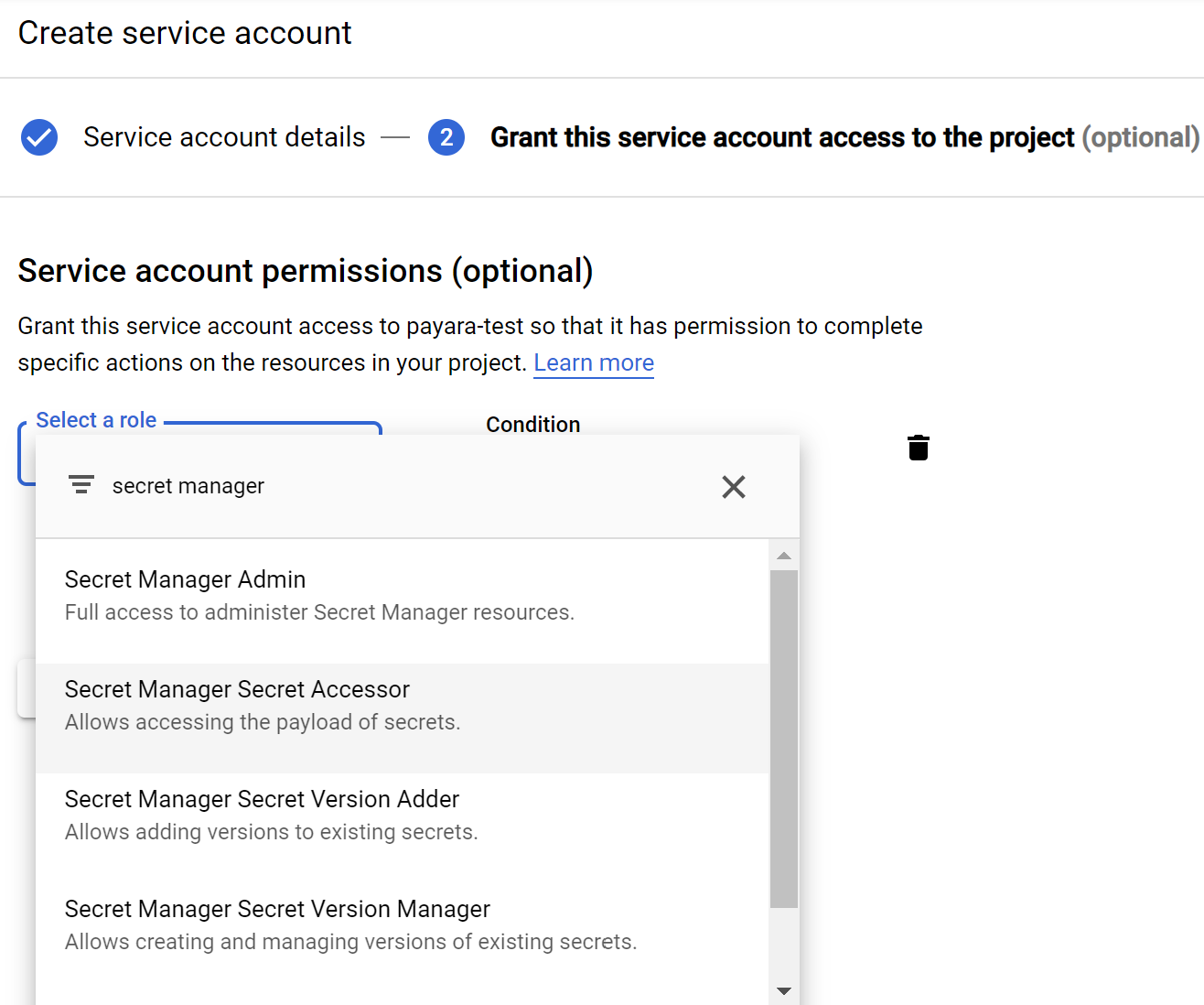
You have a selection of roles:
-
Secret Manager Admin - full admin rights to manage secrets. Recommended when you want to delete or modify secrets through Payara Server
-
Secret Manager Secret Accessor - ability to view secrets. Recommended when you only want to retrieve secrets through Payara Server
-
Secret Manager Secret Version Adder - allows setting secret values
-
Secret Manager Secret Version Manager - allows deleting secret values
Add whichever of these is appropriate for your use case.
Skip step 3 if following the wizard, as no physical user will be required to use this service account.
Next, you’ll need to download the access key for this service account.
Select the options icon for the service account you plan to use.
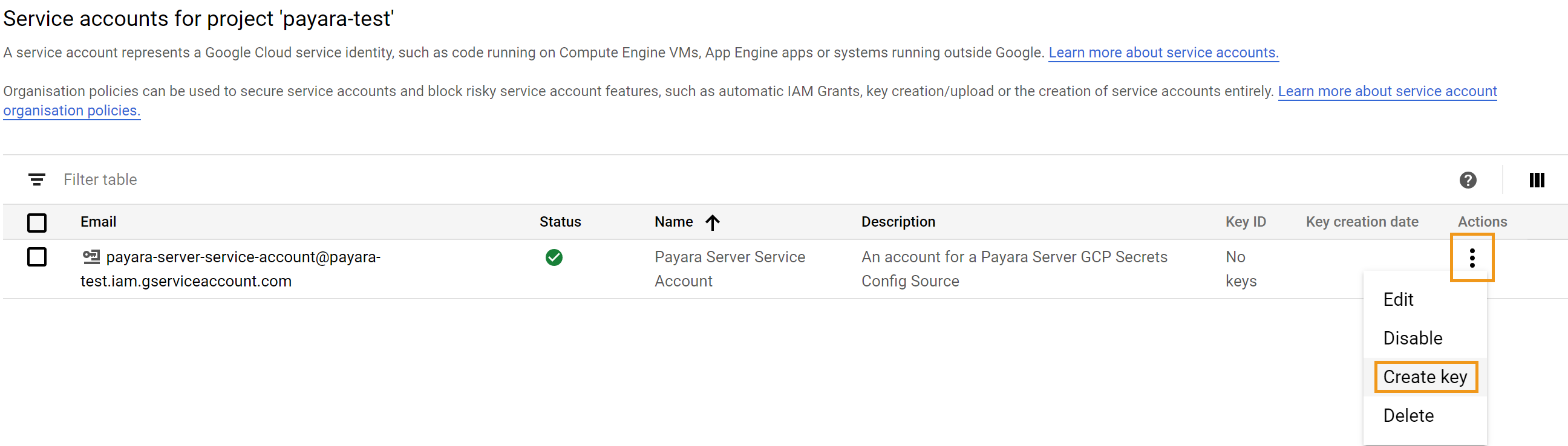
You’ll be presented with an option to download the key in JSON or P12 format. The GCP config source currently requires that the JSON format be used, so select this one.
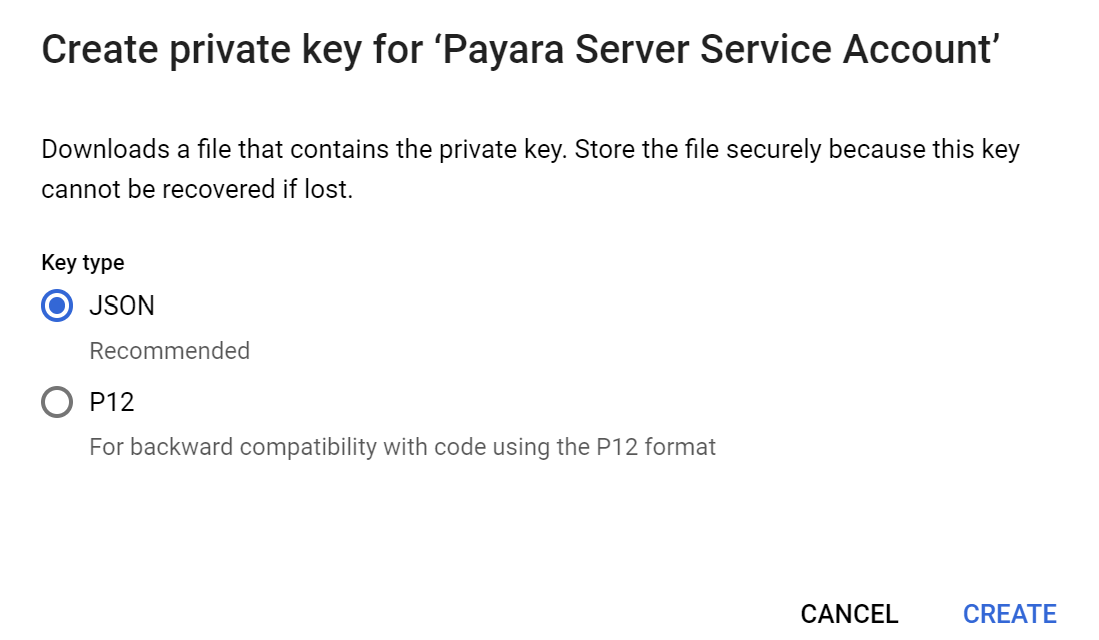
This downloaded file can now be used by Payara Server to access GCP Secrets.
Configuration
You can configure GCP Secrets either via the admin console or the asadmin utility. You’ll need the JSON key file created from the GCP console in the previous section, as well as the name of the project that you intend to use. Make sure that the GCP Secret Manager has been enabled for the specified project.
The JSON key file will be copied into the Payara Server config/ directory, so it isn’t required after passing it to the GCP Config Source configuration.
|
From the Admin Console
To configure the config source from the admin console, go to Configs → your-config → MicroProfile → Config → GCP Secrets.
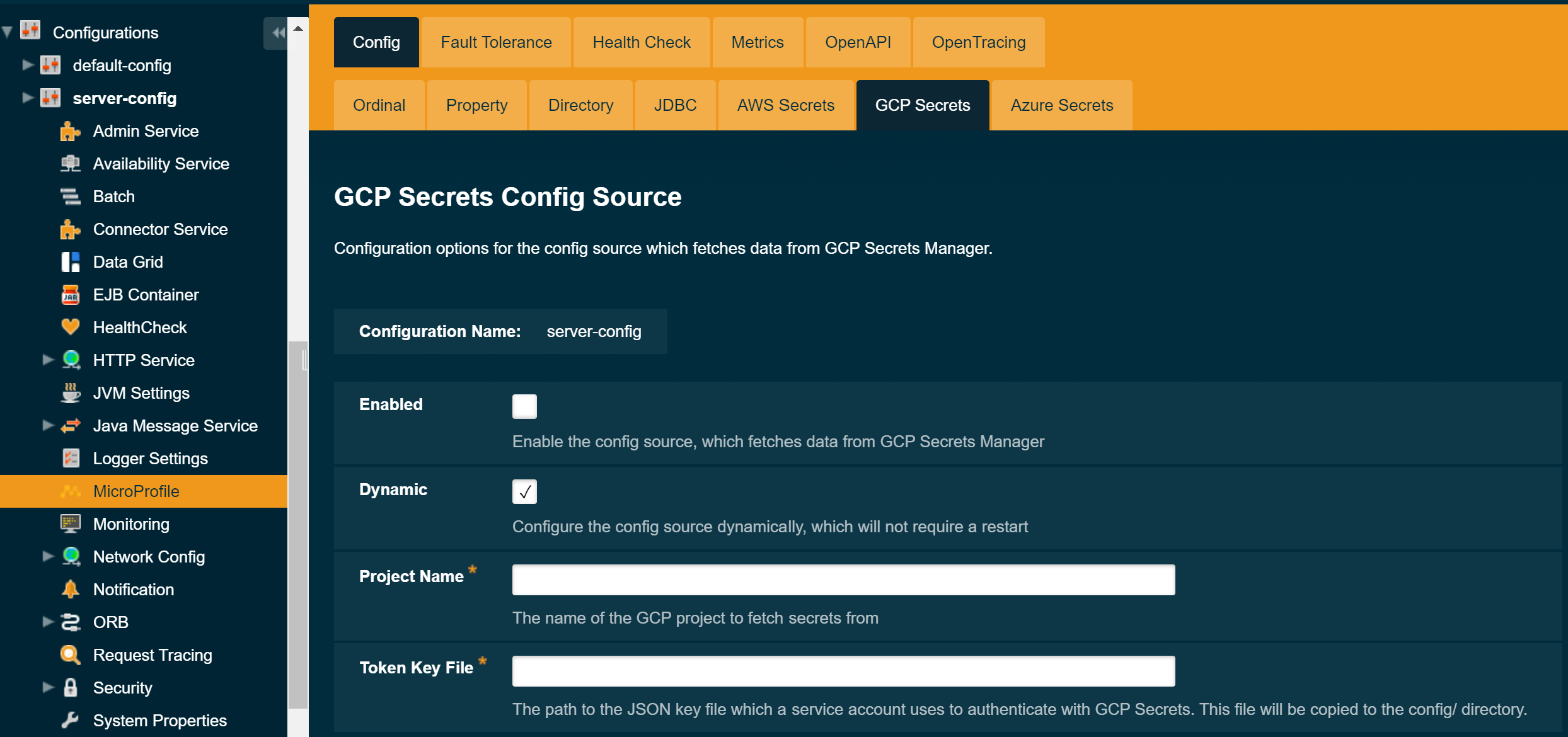
From here you can pass the absolute path to the json key file downloaded in the previous section, as well as the project name. You can also decide whether to apply these changes dynamically or on the next server restart. If the config source is enabled or disabled dynamically it will take effect across the server immediately.
From the Command Line
To configure the GCP Secrets Cloud Config Source from the command line, use the set-gcp-config-source-configuration asadmin command, specifying the required parameters like this:
asadmin> set-gcp-config-source-configuration --dynamic true --enabled true --jsonKeyFile /path/to/token/file.json --projectName project-nameYou can use the --enabled and --dynamic options to enable or disable the GCP Config Source on demand. You should pass the path to the json key file downloaded in the previous section to the --jsonKeyFile parameter.
Also, you can retrieve the current configuration for the GCP Config Source using the get-gcp-config-source-configuration asadmin command like this:
asadmin> get-gcp-config-source-configuration
Enabled Project Name JSON Key File
true payara-test payara-test-8a8aa4fbb520.jsonUsage
Provided the required roles have been assigned to the Service Account in the GCP console, the secrets can be injected into any applicable MicroProfile Config injection point as with any other Config Source. The secrets can also be fetched, created and deleted from the asadmin utility.
To fetch a secret from GCP Secret Manager:
asadmin> get-config-property --source cloud --sourceName gcp --propertyName mysecret
secretvalueTo create or change a secret from GCP Secret Manager:
asadmin> set-config-property --source cloud --sourceName gcp --propertyName mysecret --propertyValue secretvalueTo delete a secret from GCP Secret Manager:
asadmin> delete-config-property --source cloud --sourceName gcp --propertyName mysecret