AWS Cloud Config Source
The AWS cloud config source takes configuration properties from AWS Secrets Manager.
AWS Secret Creation
The AWS cloud config source takes configuration from a single named secret in a JSON format, with each object key being a config property name. To create a secret of this format, you must first go to the AWS secret manager home: https://console.aws.amazon.com/secretsmanager/home.
Once you’ve logged in, click the button to create a new secret. From here, you should specify the type as Other type of secrets. You’ll be able to enter your config properties in a key/value format below, or leave blank for configuring through Payara Server.
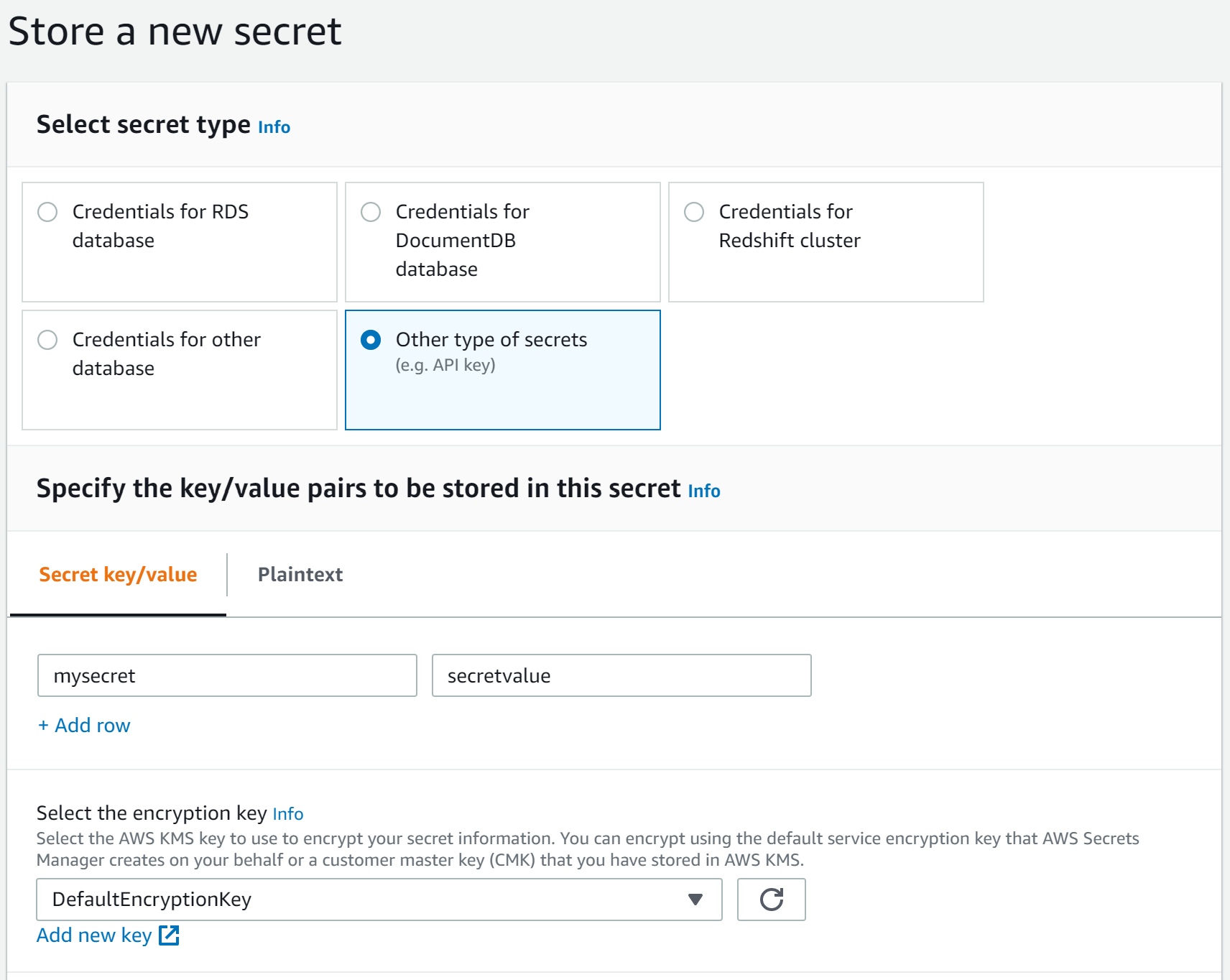
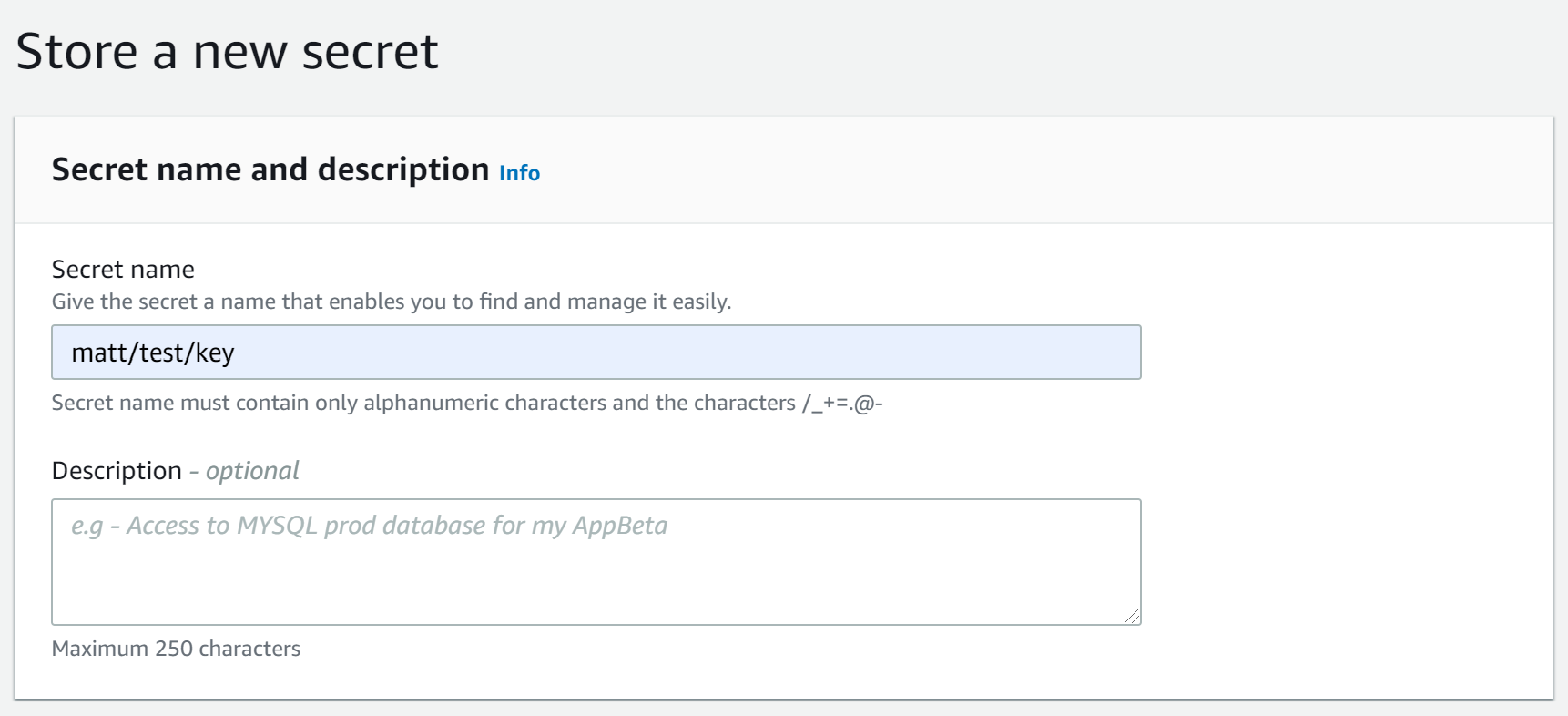
On the next screen, you’ll be able to enter your secret name. This will need giving to Payara Server in order to fetch the config properties from it.
AWS IAM User
In order to connect to AWS Secrets Manager you need to know your project name as well as have an access key. Assuming you already have an AWS project and a secret created in AWS Secrets Manager, you need to create an IAM user which Payara Server will use to access your AWS Secrets.
From the AWS console, visit the IAM Users dashboard by searching 'IAM' in the top search bar. From here, head to Users in the left menu. You’ll see all your IAM users associated with this region.
From here you can create a new IAM user. Skip this step if you already have an IAM user you want to use.
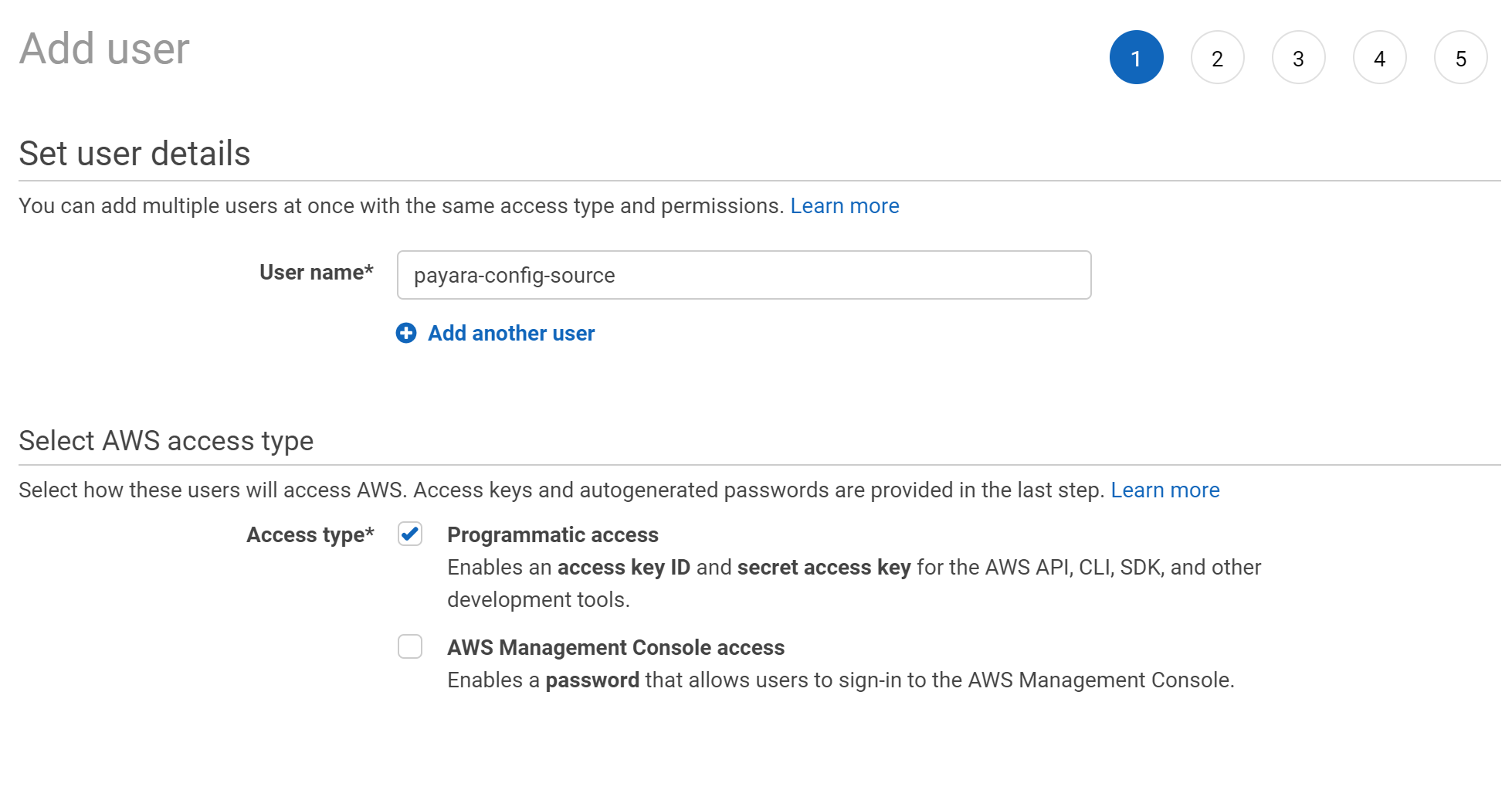
Set the IAM username. This isn’t used by Payara, but will be helpful for your own reference. Make sure you enable Programmatic access, as this will be used by Payara Server to access your AWS Secrets.
Next, select your IAM user permissions.
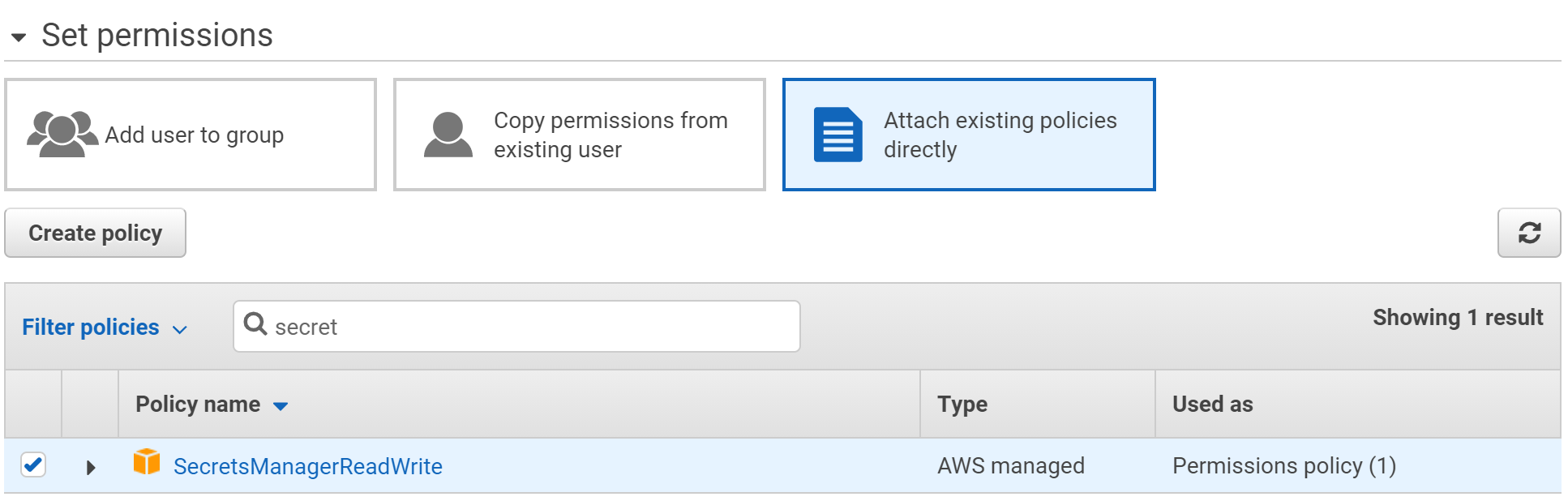
Whether you assign a group or select individual permissions, make sure the IAM user contains the SecretsManagerReadWrite permission, which will allow the user access to your secrets.
When you finish creating the IAM user, you’ll be given an access key id and secret access key. These will need to be recorded, and passed to Payara Server as Password Aliases AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY respectively.
Configuration
You can configure AWS Secrets either via the admin console or the asadmin utility. You’ll need the access key id, secret access key and secret name created from the AWS console in the previous sections, as well as the name of the AWS region. Make sure that the AWS Secrets Manager has been enabled in the specified region.
To find the region in the AWS console, check the top right dropdown:
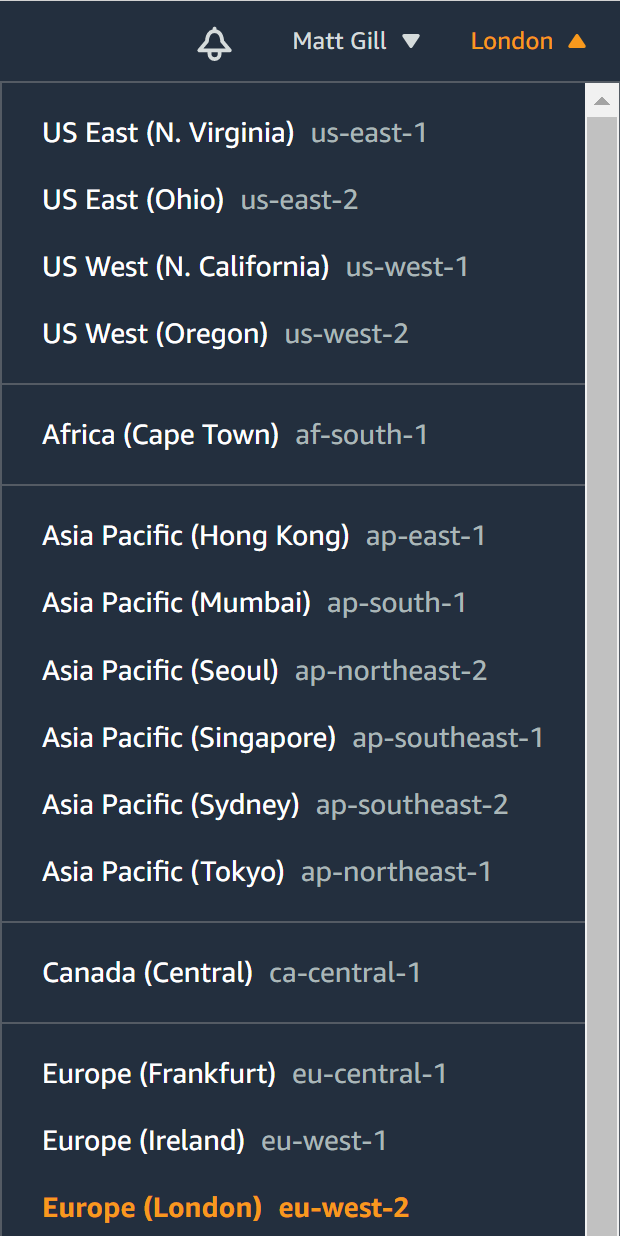
The region name is the snake-case notation, not the full words. E.g. eu-west-2.
|
From the Admin Console
To configure the AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY password aliases from the admin console, refer to the Password Aliases Admin Console configuration guide.
To configure the config source from the admin console, go to Configs → your-config → MicroProfile → Config → AWS Secrets.
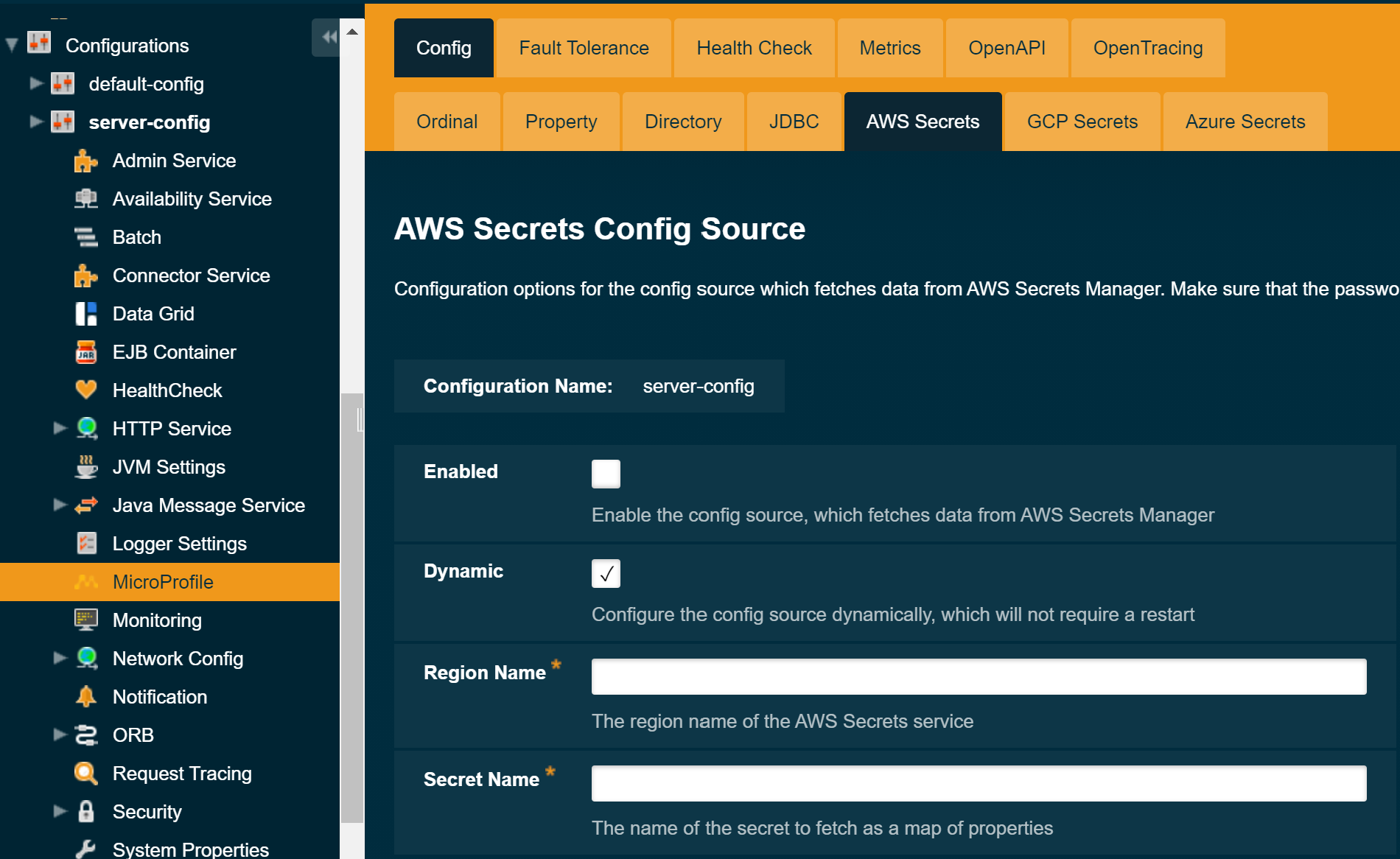
From here you can pass the name of the secret to access in AWS Secrets Manager, as well as the region name. You can also decide whether to apply these changes dynamically or on the next server restart. If the config source is enabled or disabled dynamically it will take effect across the server immediately.
From the Command Line
To configure the AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY password aliases from the command line, refer to the Password Aliases Asadmin configuration guide.
To configure the AWS Secrets Cloud Config Source from the command line, use these commands:
Usage
Provided the required roles have been assigned to the IAM user in the AWS console, the secrets can be injected into any applicable MicroProfile Config injection point as with any other configuration source.
The secrets can also be fetched, created and deleted from the asadmin utility.
To fetch a secret from AWS Secrets Manager:
asadmin get-config-property --source cloud --sourceName aws --propertyName mysecret
secretvalueTo create or change a secret from AWS Secrets Manager:
asadmin set-config-property --source cloud --sourceName aws --propertyName mysecret --propertyValue secretvalueTo delete a secret from AWS Secrets Manager:
asadmin delete-config-property --source cloud --sourceName aws --propertyName mysecret