This page documents features specific to the administration console, focusing on Payara Server enhancements.
Asadmin Recorder
This feature allows you to record the actions you take in the admin console as asadmin commands, aiding with automating or reproducing your setup across multiple Payara Server installations.
Starting and Stopping the Asadmin Recorder
You can enable or disable the asadmin recorder on its configuration page (detailed in the following section), or by using the following asadmin commands:
Once enabled or disabled, the asadmin recorder will remain enabled/disabled until specifically enabled or disabled again through the web console or using the appropriate Asadmin CLI command.
This means that the asadmin recorder will remain enabled or disabled across server restarts.
Configuring the Asadmin Recorder
To configure the asadmin recorder, navigate to the following page in the admin console: server → Asadmin Recorder:
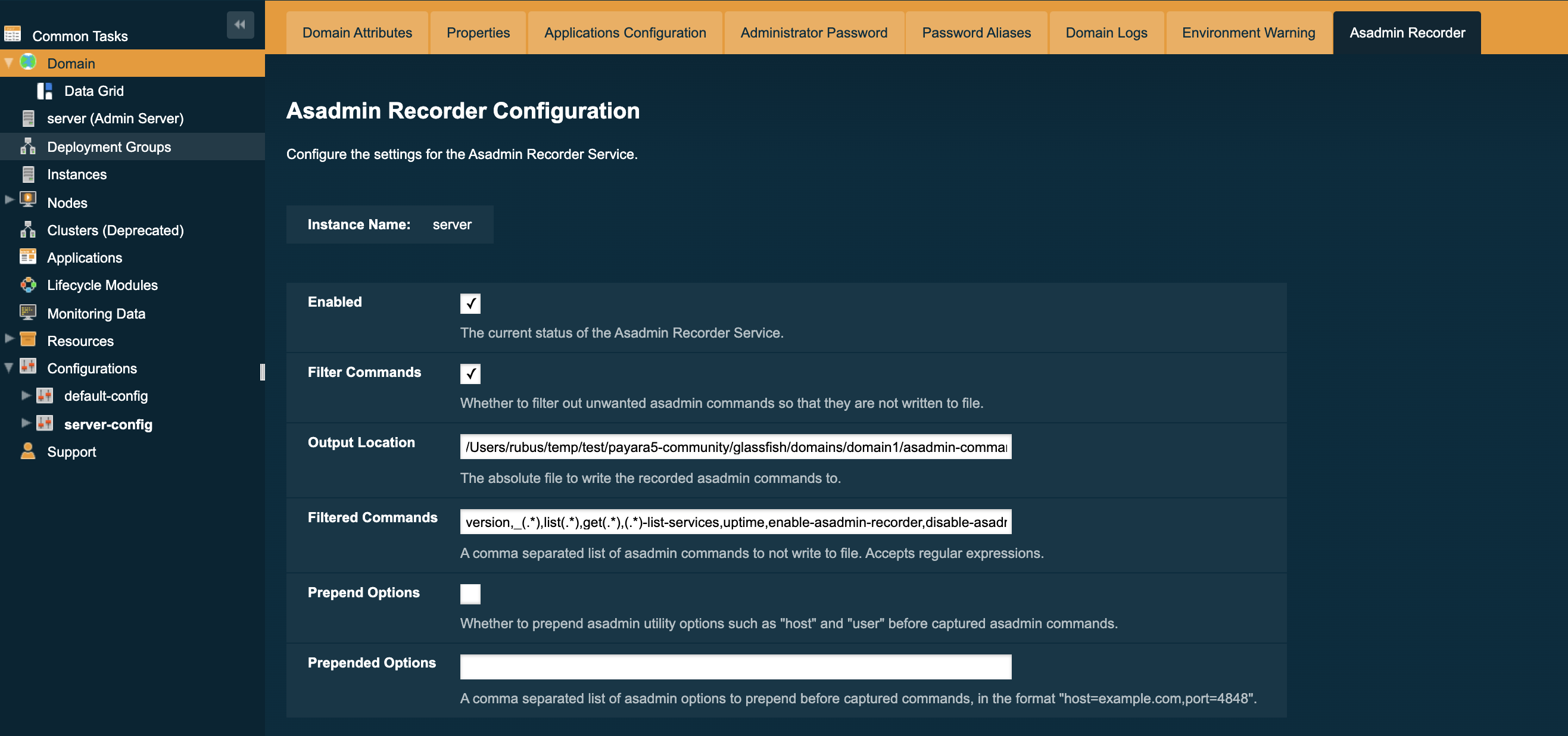
You will be presented with the following configuration options:
- Enabled
-
Sets whether the asadmin recorder service should be enabled or disabled.
- Filter Commands
-
Sets whether to exclude the
asadmincommands and regular expressions listed in the Filtered Commands setting from being recorded. - Output Location
-
The absolute file path for the
asadmincommands to be written to. This defaults to a file called asadmin-commands.txt in the domain directory. - Filtered Commands
-
A comma separated list of asadmin commands and regular expressions to be excluded from being recorded if the Filter Commands option is enabled.
The default regular expressions and asadmin commands set in the Filtered Commands option are a selection of commands and regular expressions that are typically not needed for any automation purposes, yet are still sometimes called by commands and through navigation of the admin console.
If you remove any of these commands from the filtered commands list, or choose not to filter any commands at all, the asadmin commands script is liable to get filled up with these commands. Due to this behavior, it is advised that you only add to this list, only removing the defaults if you really need to.
Be sure to click on the Save button to have any changes you make take effect.
In addition to using the admin console, you can configure the asadmin recorder service using the set-asadmin-recorder-configuration command. See set-asadmin-recorder-configuration
Running the Generated Scripts
Documentation on running asadmin scripts can be found in this section.
Admin Console Auditing Service
This feature allows users to log all actions and operations executed via the admin console for auditing purposes.
Configuring the Auditing Service
All operations executed by users with access to the admin console will be translated to events that correspond to the specific admin user that executed the operation and the asadmin command (and its parameters) that is equivalent to the operation being executed in the admin console. For example if the default admin user modifies the monitoring level of the Web Services Container, the following event will be generated:
AUDIT - admin issued command set with parameters
{
DEFAULT: [configs.config.server-config.monitoring-service.module-monitoring-levels.web-services-container=HIGH]
}The auditing service will relay these events to the Notification Service. In this manner, administrators can be alerted of suspicious activity as soon as possible.
This service can be configured from the admin console and from the command line.
From the Admin Console
The auditing service configuration can be found in the web console under Configurations → <configuration-name> → Security → Admin Audit:
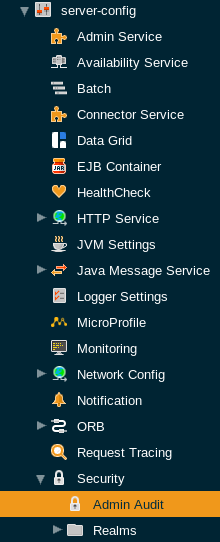
Once enabled, actions in the admin console that have a corresponding asadmin command will be sent to the Notification service.
Check the Enabled option (and the Dynamic option too if you don’t want to restart the domain) to switch the auditing service on.
The Audit Level options sets the level of operations that will be logged:
- MODIFIERS
-
(Default setting) All operations that modify the configuration of the server in some capacity.
- ACCESSORS
-
All operations query the configuration of the server in some capacity.
- INTERNAL
-
All existing operations, including internal operations of the server.
Aside from this configuration setting, you can also define which notifiers will be used to relay the admin console audit events by moving them to the Selected Notifiers box.
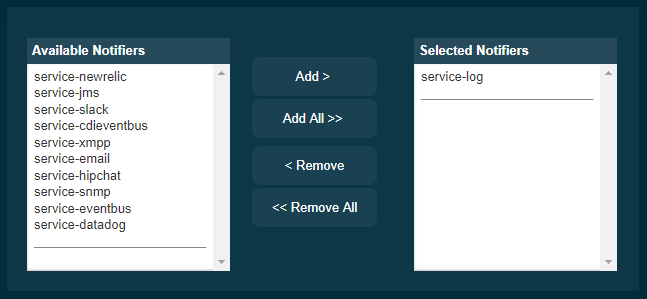
| Keep in mind that for audit events to be relayed to the selected notifiers, both the Notification Service and each selected notifier must be enabled and configured beforehand. |
| You don’t need to manually add each notifier on this screen. When enabling a notifier on its configuration screen, the server will automatically add it to the list of selected notifiers for the Admin audit service. This same result occurs when enabling the notifier using the appropriate asadmin command. |
Admin Console Environment Warning
When working with multiple shared environments, it is common for restrictions to be in place on what modifications can be allowed for a given domain. For example, the test environment cannot deviate significantly from the target production environment without potentially invalidating the test.
One way to ensure no accidental changes are made would be to revoke access to the admin console, but this has the downside of preventing engineers from seeing the current settings in the event that a bug is found.
As an alternative, Payara Server ships with a configurable warning bar to ensure any user will see a warning message in while viewing the console:
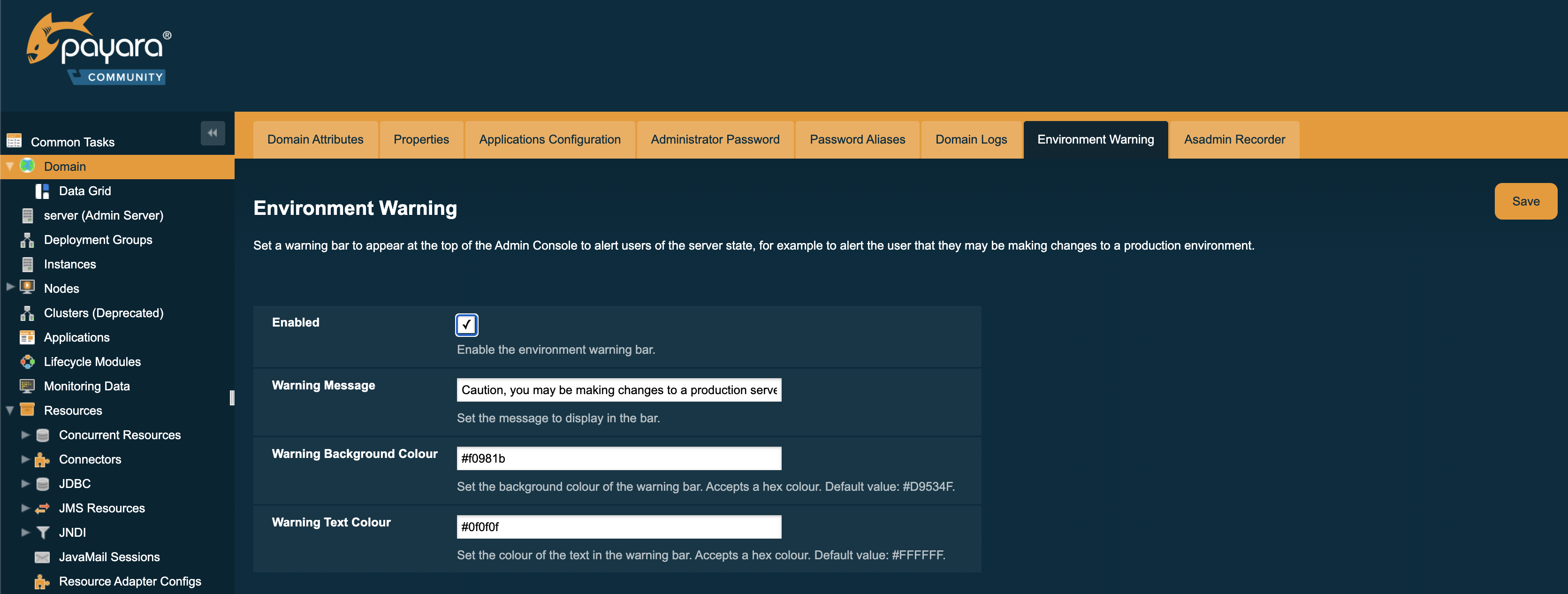
The warning can be configured in the admin console as seen in the screenshot above. There is a new "Environment Warning" tab in the "Domain" section which allows you to configure the text and colours of the warning message.
